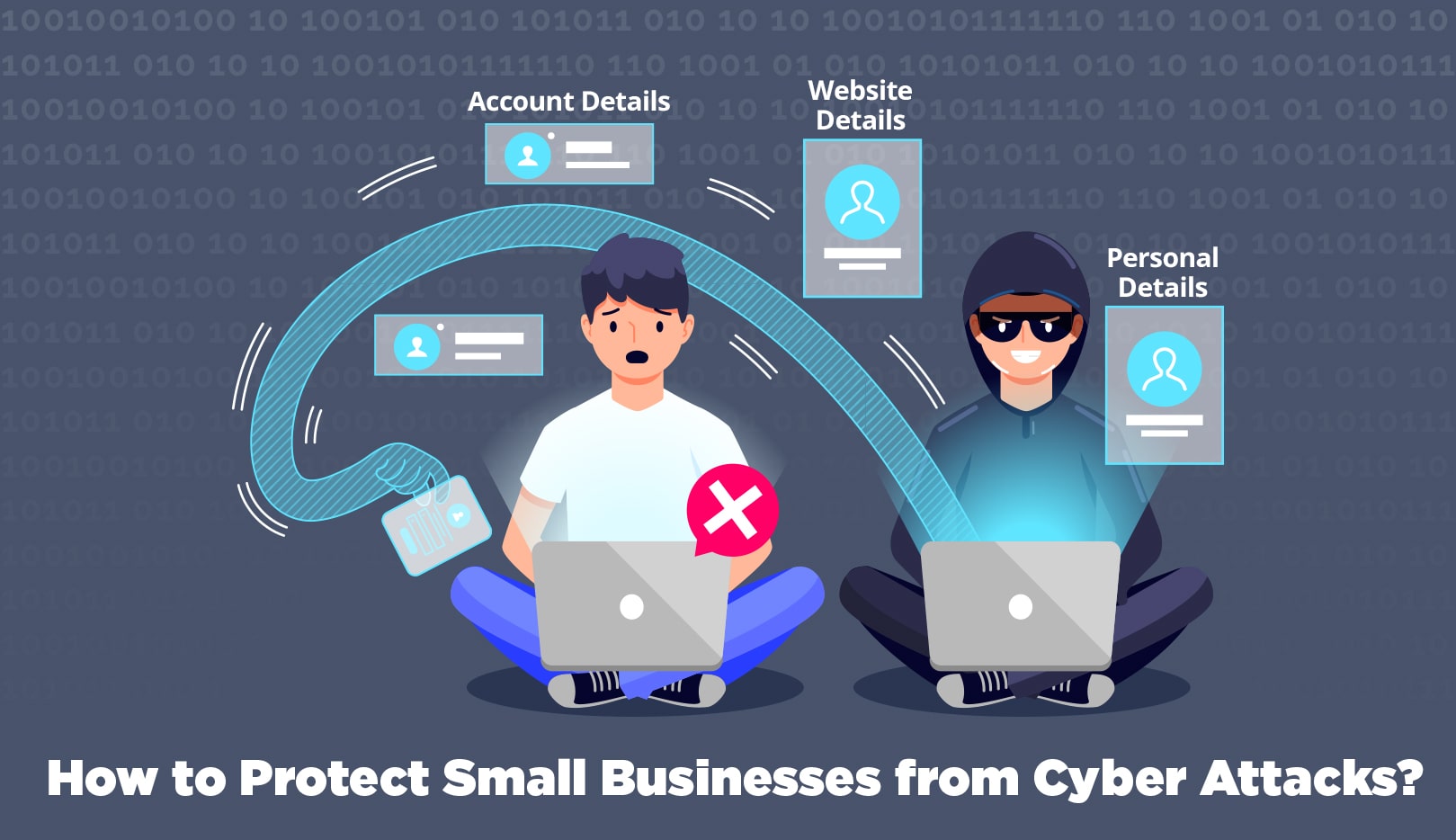
In an era where digital landscapes are integral to business operations, the specter of cyber threats looms large. The interconnected world we inhabit offers unparalleled opportunities for growth and efficiency, but it also exposes businesses to a myriad of cyber risks. From data breaches to ransomware attacks, the consequences of falling victim to cyber threats can be devastating. In this comprehensive guide, we delve into the strategies, best practices, and proactive measures that businesses can adopt to fortify their digital ramparts and protect themselves from the ever-evolving landscape of cyber threats.
1. Understanding the Cyber Threat Landscape
a. Cyber Threat Types:
To protect your business effectively, it’s crucial to understand the diverse array of cyber threats. These include phishing attacks, ransomware, malware, denial-of-service (DoS) attacks, and more. Familiarize yourself with the tactics employed by cybercriminals to infiltrate and compromise systems.
b. Risk Assessment:
Conduct a thorough risk assessment to identify potential vulnerabilities in your digital infrastructure. Assess the value of your data, the potential impact of a breach, and the likelihood of various cyber threats. This evaluation forms the foundation for a targeted and effective cybersecurity strategy.
2. Developing a Robust Cybersecurity Policy
a. Establish Clear Policies:
Develop and communicate clear cybersecurity policies within your organization. Define acceptable use of technology, guidelines for password management, rules for data handling, and protocols for reporting security incidents. Ensure that employees are aware of and adhere to these policies.
b. Regular Training and Awareness Programs:
Cybersecurity is a shared responsibility. Conduct regular training programs to educate employees about the latest cyber threats, social engineering tactics, and best practices for maintaining a secure digital environment. Awareness is a powerful defense against cyber attacks.
c. Incident Response Plan:
Develop a comprehensive incident response plan outlining the steps to be taken in the event of a cybersecurity incident. Define roles, responsibilities, and communication protocols. Regularly update and rehearse the incident response plan to ensure readiness.
3. Implementing Access Controls and Authentication
a. Role-Based Access Controls:
Implement role-based access controls to restrict access to sensitive information based on job roles and responsibilities. Grant access only on a need-to-know basis, minimizing the risk of unauthorized access to critical systems and data.
b. Multi-Factor Authentication (MFA):
Enhance authentication measures by implementing multi-factor authentication (MFA). MFA requires users to provide multiple forms of verification, such as passwords and biometrics, adding an extra layer of security to access sensitive accounts and systems.
c. Regularly Review and Update Access:
Conduct regular reviews of user access privileges and promptly revoke access for employees who no longer require specific permissions. Regularly updating access controls reduces the risk of insider threats and unauthorized access.
4. Securing Network Infrastructure
a. Firewall Protection:
Install and configure firewalls to control incoming and outgoing network traffic. Firewalls act as the first line of defense, monitoring and filtering data packets based on predetermined security rules. A well-configured firewall enhances network security.
b. Virtual Private Network (VPN):
Encourage the use of Virtual Private Networks (VPNs), especially for remote workers accessing your business network. VPNs encrypt internet connections, ensuring secure data transmission over public networks and protecting against eavesdropping.
c. Network Segmentation:
Implement network segmentation to divide your network into isolated segments. This limits the lateral movement of cyber threats within the network. Each segment can have its security controls, preventing the spread of an attack.
5. Data Encryption and Backup Strategies
a. Encrypt Sensitive Data:
Apply encryption to sensitive data, both in transit and at rest. Encryption transforms data into unreadable formats that can only be deciphered with the appropriate encryption key. This protects sensitive information even if unauthorized access occurs.
b. Regular Data Backups:
Develop and maintain robust backup and disaster recovery plans. Regularly back up critical data and store backups in secure, off-site locations. In the event of a cyber attack or data loss, a reliable backup ensures that business operations can be restored swiftly.
c. Testing Backup Restoration:
Regularly test the restoration process of your backups to ensure their integrity and reliability. This proactive measure guarantees that, in the event of a cybersecurity incident, your business can recover data effectively and minimize downtime.
6. Endpoint Security Solutions
a. Antivirus and Anti-Malware Software:
Equip individual devices (endpoints) with antivirus and anti-malware software. Regularly update these security solutions to detect and remove malicious software, providing a crucial layer of protection at the device level.
b. Endpoint Detection and Response (EDR):
Implement Endpoint Detection and Response (EDR) solutions to actively monitor and respond to cyber threats at the endpoint level. EDR tools enhance your ability to detect, investigate, and mitigate security incidents on individual devices.
c. Device Management Policies:
Establish device management policies to govern the use of personal devices within the business environment. If Bring Your Own Device (BYOD) policies are in place, ensure that these devices adhere to cybersecurity standards and pose no security risks.
7. Regular Security Audits and Assessments
a. Penetration Testing:
Conduct regular penetration testing to identify vulnerabilities in your systems. Ethical hackers simulate real-world cyber attacks to assess the security posture of your infrastructure. Addressing the findings strengthens your defenses against potential threats.
b. Vulnerability Scanning:
Perform vulnerability scans to identify weaknesses in your network and systems. Regular scans help you stay ahead of potential exploits and vulnerabilities, allowing for timely mitigation and the enhancement of overall security.
c. Compliance Audits:
Ensure compliance with industry-specific regulations and standards through regular audits. Compliance audits assess your adherence to data protection laws, cybersecurity standards, and other regulatory requirements, providing assurance and mitigating legal risks.
8. Vendor and Third-Party Risk Management
a. Due Diligence in Vendor Selection:
Before engaging with vendors or third-party service providers, conduct thorough due diligence on their security practices. Assess their cybersecurity measures, compliance with data protection regulations, and their ability to safeguard your sensitive information.
b. Secure Data Sharing Agreements:
Establish secure data sharing agreements with vendors and third parties. Clearly define the terms of data handling, storage, and access. Ensure that contractual agreements include provisions for cybersecurity standards and incident response protocols.
c. Regular Vendor Security Assessments:
Periodically assess the security posture of your vendors and third-party partners. Request and review their security assessments, penetration test reports, and compliance documentation. Regular assessments ensure ongoing alignment with your cybersecurity standards.
9. Employee Education and Social Engineering Awareness
a. Phishing Awareness Training:
Phishing attacks remain a prevalent threat. Conduct regular phishing awareness training for employees to help them recognize and avoid phishing attempts. Training should cover email, social media, and other communication channels.
b. Strict Information Sharing Policies:
Enforce strict policies regarding information sharing, especially sensitive information. Limit the disclosure of sensitive data to individuals who genuinely need access and implement controls to prevent unauthorized sharing of confidential information.
c. Two-Factor Authentication (2FA):
Enhance security against unauthorized access resulting from social engineering by implementing Two-Factor Authentication (2FA). 2FA requires users to provide additional verification beyond passwords, adding an extra layer of protection to sensitive accounts.
10. Continuous Monitoring and Threat Intelligence
a. Security Information and Event Management (SIEM):
Implement Security Information and Event Management (SIEM) solutions to monitor and analyze security events across your network. SIEM tools provide real-time insights into potential security incidents, enabling timely responses.
b. Threat Intelligence Integration:
Integrate threat intelligence feeds into your cybersecurity strategy. Stay informed about emerging threats, vulnerabilities, and attack patterns. Proactively leveraging threat intelligence enhances your ability to anticipate and mitigate cyber threats before they manifest.
c. Behavioral Analytics:
Employ behavioral analytics to detect anomalies in user behavior and network activity. Behavioral analytics tools use machine learning algorithms to identify patterns that deviate from normal behavior, providing early indications of potential security threats.
11. Regular Software Patching and Updates
a. Patch Management Procedures:
Establish robust patch management procedures to ensure that software, operating systems, and applications are promptly updated. Regularly applying patches and updates addresses known vulnerabilities and reduces the risk of exploitation by cybercriminals.
b. Automated Patching Solutions:
Implement automated patching solutions to streamline the update process. Automated tools can efficiently manage and deploy patches across your network, reducing the window of exposure to potential security vulnerabilities.
c. Legacy System Evaluation:
Evaluate the security implications of legacy systems within your infrastructure. If certain systems are no longer supported by vendors and cannot receive security updates, consider upgrading or replacing them to mitigate security risks.
12. Legal and Regulatory Compliance
a. Data Protection Compliance:
Ensure compliance with data protection regulations applicable to your business. Depending on your location and industry, regulations such as GDPR, HIPAA, or CCPA may apply. Regularly assess and update your data protection practices to align with evolving compliance requirements.
b. Industry-Specific Regulations:
If your business operates in a regulated industry, stay abreast of industry-specific regulations. These may include financial regulations, healthcare standards, or cybersecurity frameworks. Compliance with industry regulations is crucial for avoiding legal repercussions.
c. Privacy Policies and Notices:
Maintain transparent privacy policies and notices. Clearly communicate to your customers and stakeholders how their data is collected, stored, and used. Regularly update these policies to reflect changes in data practices or privacy regulations.
In Conclusion: A Resilient Future for Your Business
In the ever-evolving landscape of threats and vulnerabilities, fortifying the security of your business is not a one-time endeavor but a continual process. By implementing the strategies and best practices outlined in this comprehensive guide, you empower your organization to navigate the complexities of the digital realm with resilience and confidence.
Remember, cybersecurity is not just a technical consideration; it is a cultural mindset that permeates every facet of your business. From employee education and access controls to continuous monitoring and compliance, each aspect contributes to the creation of a secure and robust environment for your organization to thrive.
As you embark on the journey to protect your business from cyber threats, view it as an investment in the longevity and success of your enterprise. Stay vigilant, adapt to emerging threats, and cultivate a cybersecurity-first mindset to ensure that your business remains resilient in the face of an ever-changing landscape of challenges and opportunities. By embracing cybersecurity as an integral part of your business strategy, you not only safeguard sensitive information but also foster trust among your customers, partners, and stakeholders in an increasingly interconnected digital world.